TWO-FACTOR AUTHENTICATION
SESSION CODE
STRONGER ENCRYPTION
TRANSPARENT TO FIREWALLS
NEXT-GENERATION REMOTE DESKTOP SECURITY FOR YOUR BUSINESS
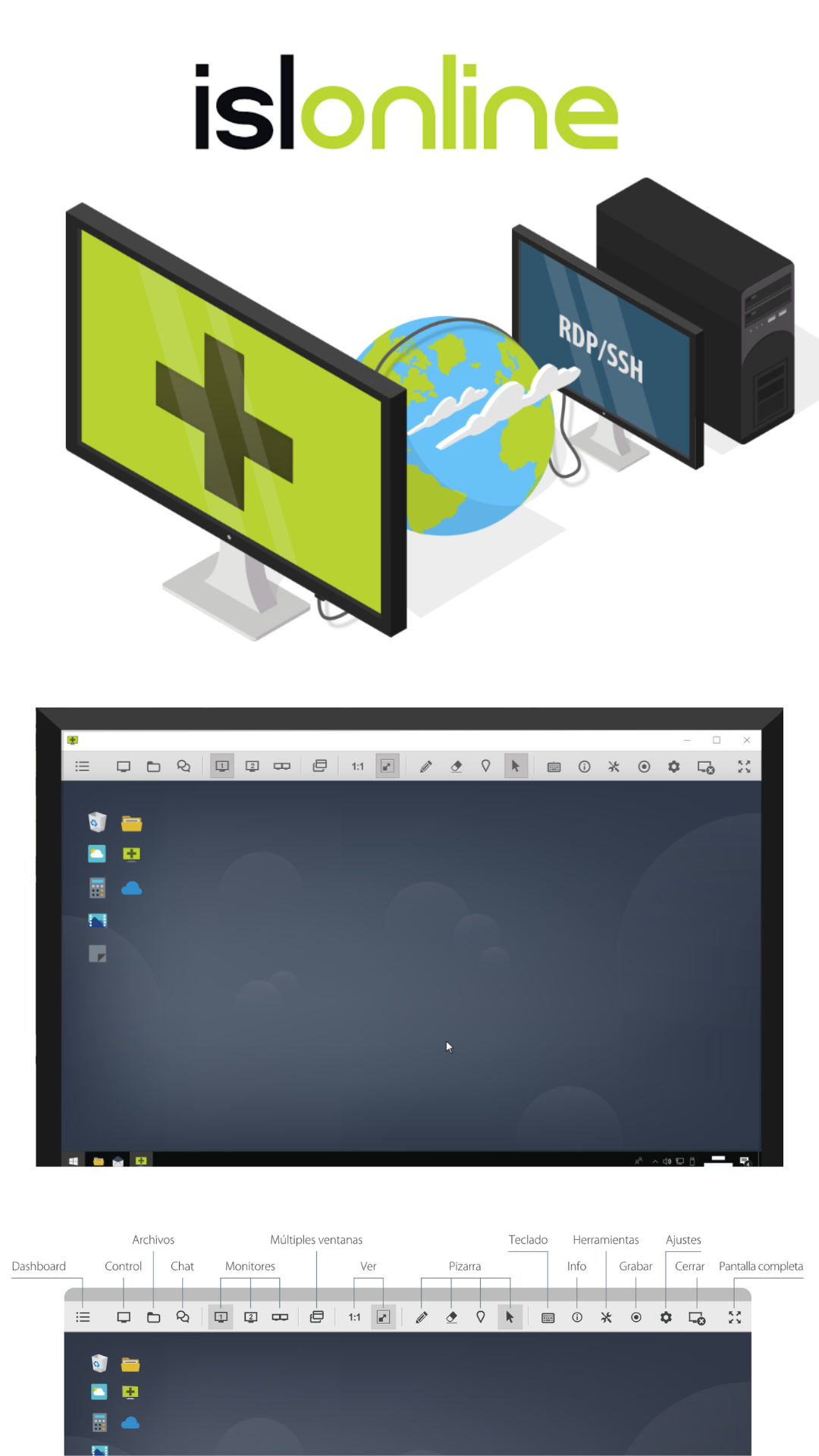
ISL Online, since 2003, specializes in remote access technology for IT professionals in over 100 countries. Our solution enables remote control of Windows, Mac, Linux, and mobile devices, available in the cloud and on-premises. ISL Online is part of the XLAB Group, headquartered in Slovenia with offices in Switzerland, the UK, and the US.
ADVANCED PROTECTION
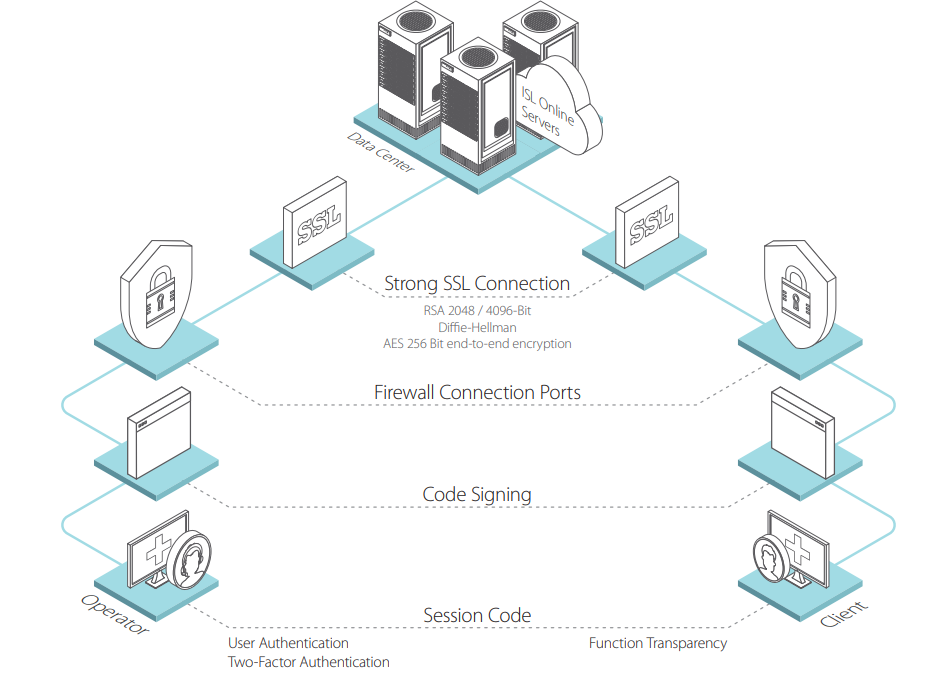
At ISL Online, we prioritize information security when establishing connections with remote computers. We implement robust measures to meet the high security standards our customers demand. We use 2048/4096-bit RSA encryption for public-private key exchange, followed by 256-bit AES encryption to protect data traffic. In addition, we employ unique session codes that are automatically invalidated after each connection, and we offer two-factor authentication to add an extra layer of protection. ISL Online is also compatible with existing firewalls, initiating outbound connections through standard ports such as 7615, 80, or 443, without requiring any additional configuration.
Information Security
At ISL Online, security is paramount. We implement multiple layers of protection to secure remote connections:
- Strong Encryption: We use 2048/4096-bit RSA and 256-bit AES to encrypt data.
- Unique Session Code: Each session uses a unique code that is invalidated after the connection.
- Two-Factor Authentication (2FA): We add an extra layer of security.
- Firewall Compatibility: Works with existing firewalls without additional configuration.
- Secure SSL Connection: We use SSL with RSA and Diffie-Hellman to secure data transmissions.
Additional Security Measures
- ISO 27001:2013 Certification: We comply with international safety standards.
- Port Filtering: Port management for secure access.
- Whitelist/Blacklist: IP/MAC-based access control.
- Code Signing: Ensures the authenticity and non-modification of the software.
- Security Audits: We conduct regular penetration tests to identify vulnerabilities.
- Brute Force Attack Protection: We limit failed login attempts.